New: managing your fine-grained permissions
by Oshrat Nir on Sep 12, 2022

Security and access control to resources are top of mind for everyone running Kubernetes. And while powerful, role-based access control (RBAC) in Kubernetes is not simple. Giant Swarm management clusters are no different. Trying to control access to the various resources required to manage workload clusters and apps is tricky, cumbersome, and error-prone.
Let's use an example to clarify the concepts we are discussing.
To create workload clusters, you need multiple permissions to create many types of resources. You will, of course, want to be able to see your results, so you need permission to list and get these resources.
Using CLI (e.g., kubectl auth can-i command) to verify and maintain RBAC permissions is not a good solution. You will have a hard time identifying if a specific user can, in fact, create a cluster since there is no single CLI command that provides this information in a simple way.
What's new
Our web interface now offers a way to easily aggregate RBAC rules into meaningful use cases. Let's take managing clusters as an example. Using this functionality, you can be confident that your (single) query covers all the options that apply to the specific actor/permissions view combination.
This is part of a larger initiative (that includes access control as well) in which we strive to enable more users to use the management cluster's Kubernetes API (Management API). This is one of the tools we have introduced to ensure governance and increase security while still enabling flexibility in defining and managing users.
Definitions
Actors
| Myself | The current authenticated user |
| Group | The specified group |
| User | The specified user |
| Service account | The specified service account |
Permissions view
| Global | Use cases that require permissions outside the organization namespace |
| For organizations* | Use cases applicable to specified organization namespaces |
*Organizations are defined in this context as a means to organize resources like clusters and apps so that different entities are isolated from each other.
How it works
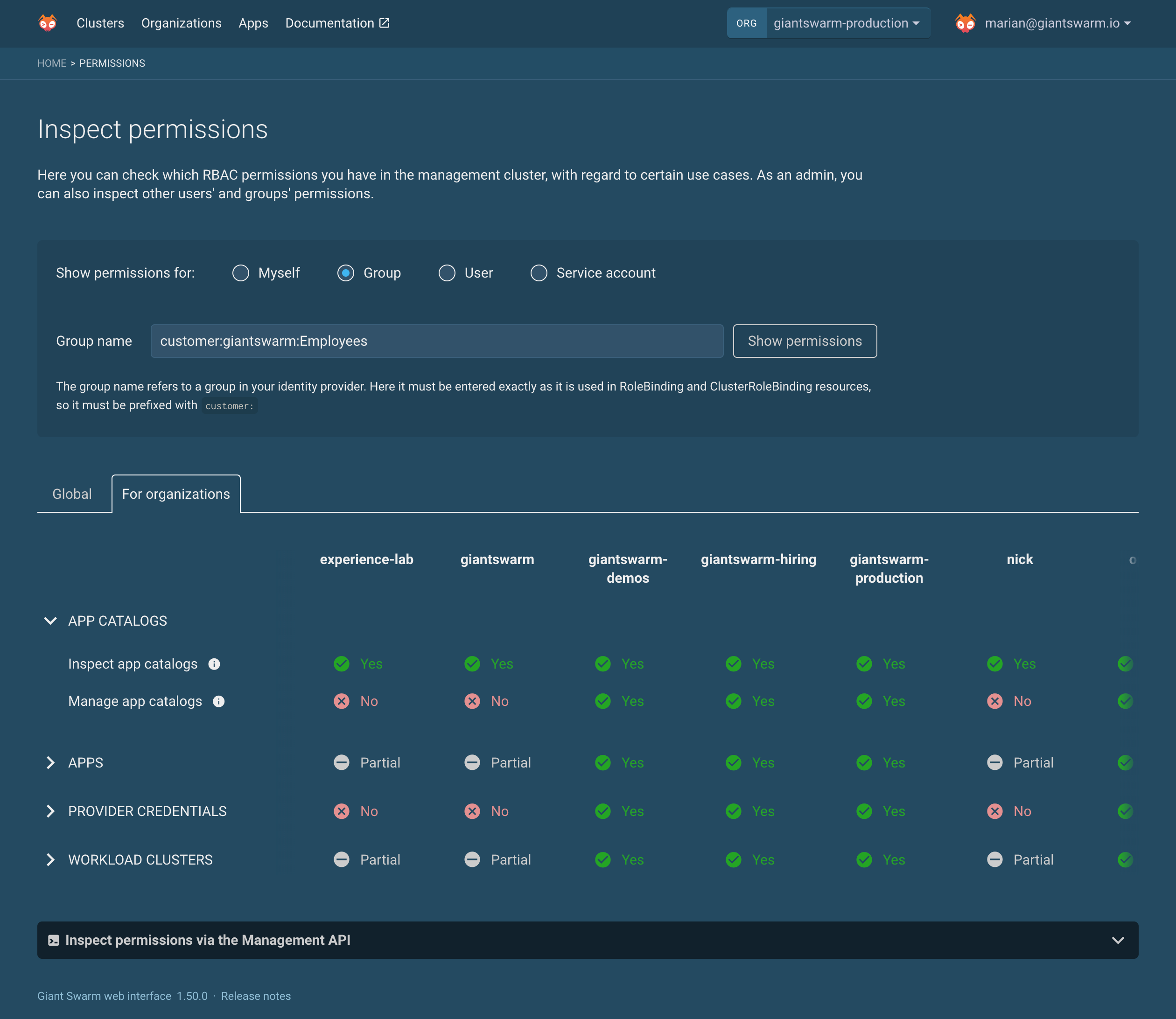
An administrator can inspect permissions for groups, users, and service accounts.
You can view permissions either on a global level (use case: managing namespaces) or divided by organizations, provided you have access to them, with use cases by organization.
Typing in a group name and clicking on show permissions shows you the actual permissions in the Management API. You can then view Global permissions for the specified Group name and on the For organizations tab you get the information per organization.
Summary
As mentioned earlier, this is part of a larger initiative for allowing users access to the Management API. Specifically for inspection of permissions, we have a lot of ideas on how to continue to improve this. So stay tuned to this space.
If you are curious about how Giant Swarm can help you with governance and security, reach out to us, and let's have a conversation.
You May Also Like
These Related Stories

Giant Swarm vs OpenShift
At Giant Swarm, we’ve often been asked to compare our infrastructure with that of Red Hat OpenShift. We’d like to shed some light on this subject and …

Production-grade Kubernetes Now in an Azure Region near You
We’re thrilled to announce that Giant Swarm is now available on Azure. This adds to the support we already have for AWS and on-premise installations a …

How Giant Swarm Enables a New Workflow
By now we all know that Amazon AWS changed computing forever and it actually started as an internal service. The reason for the existence of AWS is pr …